🤩 배경
스프링 부트 2 버전에서는 Keycloak 클라이언트 어댑터(KeycloakWebSecurityConfigurerAdapter)를 사용하여 애플리케이션에 쉽게 연결해서 사용했다. 하지만 스프링 부트 3부터 일부 클래스, 메서드, 속성 및 어노테이션이 제거되었다.
해당 포스트에서는 스프링 부트 3 환경에서 Spring Security Oauth2와 KeyCloak을 연결해서 사용하는 방법을 공유한다.
1. Dependency 추가
우선, oauth2 resource service 의존성을 추가한다.
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-oauth2-resource-server</artifactId>
</dependency>2. properties 설정
Spring Security에 관련 설정을 추가한다.
spring.security.oauth2.resourceserver.jwt.issuer-uri = http://localhost:8180/realms/spmia-realm
spring.security.oauth2.resourceserver.jwt.jwk-set-uri = ${spring.security.oauth2.resourceserver.jwt.issuer-uri}/protocol/openid-connect/certs
jwt.auth.converter.resource-id = {userid}
jwt.auth.converter.principal-attribute = preferred_username
해당 정보는 KeyCloak - Realm settings 메뉴에서 Endpoints - OpenID Endpoint Configuration에서 확인 가능하다.

OpenID Endpoint Configuration을 클릭하면 다음과 같은 정보를 얻을 수 있다.
그중에서 issuer, jwks_uri에 대한 정보를 properties에 입력하면 된다.

3. 코드 작성
우선, properties에서 설정한 jwt 구성 정보를 애플리케이션으로 가지고 오는 Properties 클래스를 생성한다.
@Data
@Validated
@Configuration
@ConfigurationProperties(prefix = "jwt.auth.converter")
public class JwtAuthConverterProperties {
private String resourceId;
private String principalAttribute;
}
다음으로, JWT 데이터에서 역할 등의 정보를 추출해서 JwtAuthenticationToken(Authentication)으로 변환하는 Convert 클래스를 추가한다.
@Component
public class JwtAuthConverter implements Converter<Jwt, AbstractAuthenticationToken> {
private final JwtGrantedAuthoritiesConverter jwtGrantedAuthoritiesConverter = new JwtGrantedAuthoritiesConverter();
private final JwtAuthConverterProperties properties;
public JwtAuthConverter(JwtAuthConverterProperties properties) {
this.properties = properties;
}
@Override
public AbstractAuthenticationToken convert(Jwt jwt) {
Collection<GrantedAuthority> authorities = Stream.concat(
jwtGrantedAuthoritiesConverter.convert(jwt).stream(),
extractResourceRoles(jwt).stream()).collect(Collectors.toSet());
return new JwtAuthenticationToken(jwt, authorities, getPrincipalClaimName(jwt));
}
private String getPrincipalClaimName(Jwt jwt) {
String claimName = JwtClaimNames.SUB;
if (properties.getPrincipalAttribute() != null) {
claimName = properties.getPrincipalAttribute();
}
return jwt.getClaim(claimName);
}
private Collection<? extends GrantedAuthority> extractResourceRoles(Jwt jwt) {
Map<String, Object> resourceAccess = jwt.getClaim("resource_access");
Map<String, Object> resource;
Collection<String> resourceRoles;
if (resourceAccess == null
|| (resource = (Map<String, Object>) resourceAccess.get(properties.getResourceId())) == null
|| (resourceRoles = (Collection<String>) resource.get("roles")) == null) {
return Set.of();
}
return resourceRoles.stream()
.map(role -> new SimpleGrantedAuthority("ROLE_" + role))
.collect(Collectors.toSet());
}
}
마지막으로, Spring Security에서 Oauth2 ResourceServer 설정을 추가한다.
@Configuration
@EnableWebSecurity
@EnableMethodSecurity(jsr250Enabled = true)
@RequiredArgsConstructor
public class SecurityConfig {
private final JwtAuthConverter jwtAuthConverter;
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
http.authorizeHttpRequests(authz -> authz.anyRequest().authenticated())
.oauth2ResourceServer(authz -> authz.jwt(jwtConfigurer -> jwtConfigurer.jwtAuthenticationConverter(jwtAuthConverter)))
.sessionManagement(authz -> authz.sessionCreationPolicy(SessionCreationPolicy.STATELESS))
.csrf(authz -> authz.disable());
return http.build();
}
}
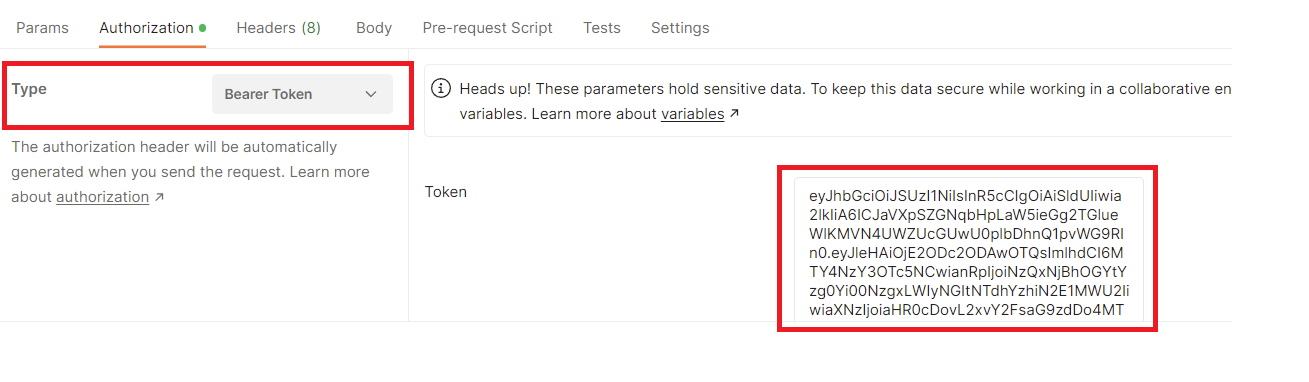
4. 테스트
KeyCloak 서버에서 인증 후 access_token 값을 Bearer Token 방식으로 전달하면 된다.

REFERNECE
https://medium.com/geekculture/using-keycloak-with-spring-boot-3-0-376fa9f60e0b
'Spring' 카테고리의 다른 글
| Spring message ChannelInterceptor 메서드 특징 (0) | 2023.07.23 |
|---|---|
| Spring RedisSerializer 종류와 특징 (0) | 2023.07.15 |
| Spring Boot 3 + JPA를 활용한 Liquibase 실습하기 (4, final) (0) | 2023.06.06 |
| 동적 리스트 바인딩 문제 해결하기 (java.lang.IndexOutOfBoundsException: Index: 256, Size: 256) (0) | 2023.06.06 |
| Spring Boot 3 + JPA를 활용한 Liquibase 실습하기 (3) (0) | 2023.05.29 |




댓글